Leaked Credentials
Notice: Patent Pending
Certain technical details, processes, methods, and innovations described or illustrated on this page have been intentionally omitted or redacted to protect confidential trade secrets and patentable subject matter.
One or more patent applications have been filed (or are in preparation) with respect to the technologies and inventions referenced herein. These inventions are currently Patent Pending in the United States and/or other jurisdictions.
>31Bn
Leaked credentials from around the world
>500M
Unique profiles developed
17.5k
Dark web user profiles, mapped to the surface web using breach data
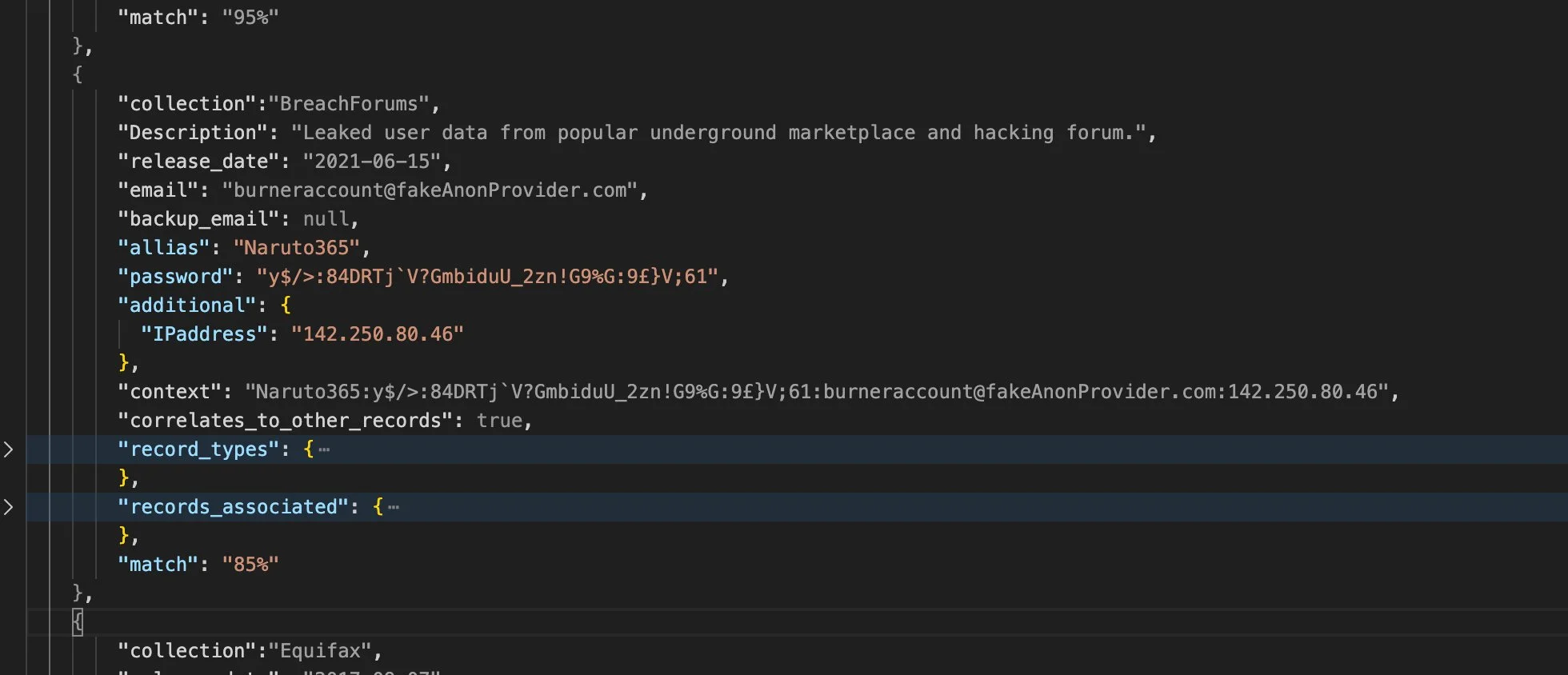
Leaked Credentials
Dendrite’s proprietary database and record structure enables defenders, including cybersecurity firms, companies, researchers, and government agencies to rapidly query leaked credential databases (aka “Breach Data”) for analysis Easily queryable through our CLI, API or Unified Web Platform and pre-correlated to records from our other data sources, our leaked credential database holds more than 31 billion records, dynamically masked in a manner that protects public privacy while providing maximum intelligence value to our clients and partners.
How it’s used:
-
Set alerts or cross-reference leaked credentials against your user base, automatically triggering password reset enforcement while preemptively securing sensitive resource access and preventing follow-on attacks.
-
Leaked data often includes contextual details, enabling attackers to craft personalized phishing emails or smishing (SMS phishing attacks, increasing their success rates. Dendrite clients leverage this data to mitigate risks facing their employees and organization from this attack vector.
-
Continuously updated and pre-correlated to our other data sources, breach data empowers CTI professionals to streamline complicated task chains, such as threat actor tracking & attribution and triage high-risk exposures (e.g., privileged accounts).
-
By studying credential leaks, defenders can identify trends, such as commonly used weak passwords or vulnerable hashing algorithms. This informs better security policies, like banning reused passwords or implementing password strength meters.
-
Un-edited, un-masked versions of this dataset are available to law enforcement agencies (LEA), Defense Contractors, and trusted organizations from Tier 1 countries.
Part of the Complete Data Platform
Each of our core capabilities is represented by a fully independent extract, transform and load (ETL) pipeline, enabling Dendrite to ingest and correlate data between technically disparate resources and infrastructure. All leaked credential records are enriched with many hundreds of additional data points, linking dark web services, users, communication hubs and historical records to Command & Control servers and more.
Use-Cases in Contrast: Adversaries vs. Defenders
Breach data is most commonly associated with malicious actors and red team engagements. However, this data serves as an extremely high fidelity data set to intelligence and blue team analysts in your organizations defense.
So many things in development
Our pursuit of perfection in enterprise defense mandates that every stone is upturned - no matter how fringe the case or how difficult the path to development may be.
With dozens of POC’s and MVP’s in the works, our researchers and development teams work to continuously deliver bleeding edge capabilities to the Dendrite Unfed Platform and data sources.
Get in touch
Interested in learning more, scheduling a demo or speaking with our team? Get in contact with us - we'd love to hear from you.